Cyber Criminals Are Targeting You With COVID-19 Emails
Cyber criminals are taking advantage of the fear and uncertainty surrounding COVID-19 and using stimulus check offers as lure for phishing attempts.
by Marcus
Posted on March 30 2020
With the US and other nations passing legislation for an economic stimulus many cyber criminals have ramped up phishing attacks using the promised payouts as bait. For example even before US President Donald Trump signed the stimulus bill into law, our monitoring services had picked up an uptick of malicious messages disguised as information about stimulus checks, unemployment benefits and small business loans.
The most common reason for these emails have been centered on a malicious file known as Zloader or Terdot. While this is not new, COVID-19 and the fear and uncertainty surrounding it has created a fresh opportunity for cyber criminals.
The most common form of this scam is a message which contains a doc or docx file that the email claims must be filled out in order to receive the money. The document when opened activates a download which then delivers Zeus Sphinx.
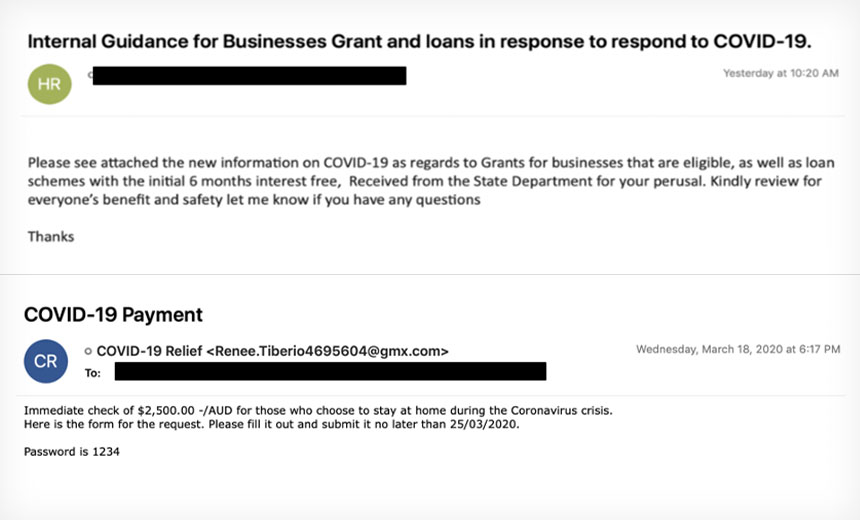
Zeus Sphinx uses web injection to alter certain pages (typically baking related pages) to trick the user into entering personal login information and authentication codes which is then sent back to the cybercriminal. We have also been monitoring messages with the subject: "Internal Guidance for Businesses Grant and loans in response to respond to COVID-19," this seems to be mostly targeting small businesses and is an attempt to trick people into entering their Microsoft office sign in information.
These threats are constantly evolving and is one of the most important features of ACTIVE monitoring by /MT. According to Barracuda Networks, between March 1 and March 23 they tracked 9,100 COVID-19 related phishing emails, it was only 1,180 the month before, and 137 the month before that. These attacks are getting more common. And it is important that you get out ahead of them before falling victim. Get your few security audit, or contact us today about ACTIVE monitoring to make sure you stay safe.
Category: Security